Group Policy Management Console Scripting Samples Download
- Group Policy Management Console Scripting Samples Download Free
- How To Access Group Policy
- Group Policy Management Software
- Group Policy Management Console X64
- Group Policy Management Windows 10

- NOTE: You can use any name you like, but it would make it easier for you to know what user (ex: Test) or group this “specific” group policy MMC console was for later if you included the user or group name. Move the MSC file (ex: Non-Administrators-Group-Policy.msc) to where you would to keep it saved at.
- Download resources and applications for Windows 10, Windows 8, Windows 7. Group Policy Management Console Scripting Samples KevinSchultz-MS FT The following is a collection of Group Policy Management Console (GPMC) scripting samples.
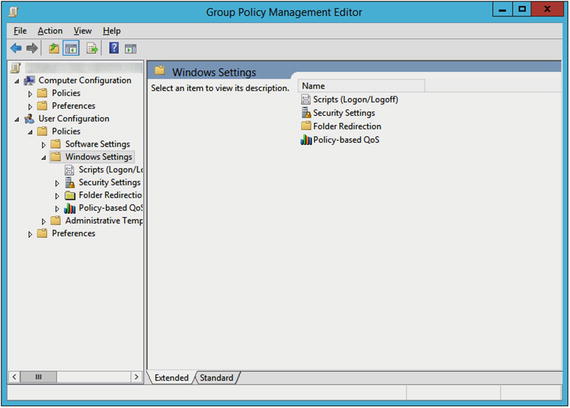
- The Group Policy Management Console (GPMC) is designed to help and simplify Group Policy management by providing a single place for managing core aspects of Group Policy. You can think of the GPMC as a one-stop resource for managing your Group Policy needs.
There are a couple of ways administrators can manage Group Policy, including Local Group Policy Editor, Group Policy Management Console (GPMC) and PowerShell. Local Group Policy Editor is a snap-in for the Microsoft Management Console. PowerShell commands were introduced in Windows Server 2008.
The following information describes the Group Policy Management Console (GPMC) scripting samples. These samples were originally found in the '%programfiles%GpmcScripts' directory after you installed the GPMC, and now can be found on the TechNet Code Gallery. You can execute the scripts at the command prompt. The scripts send output to the Command Prompt window. Run the scripts using the CScript.exe application.
The following script samples address administrative tasks:
There are also script samples that perform the following queries:
Backing Up an Individual GPO
The BackupGPO.wsf sample backs up a Group Policy object (GPO) to a specified backup directory. You can specify the GPO either by its name or by its GPO ID. The backup directory and the GPO must already exist. You can use the Comment parameter to specify an optional comment for the backup.
Usage: BackupGPO.wsf <GPO Name> <BackupLocation> [/Comment:<Comment>] [/Domain:<DNSDomainName>]
Example: BackupGPO.wsf TestPolicyGPO servershareGPOBackups /Comment: 'Weekly backup' /Domain:example.microsoft.com
Backing Up the GPOs in a Domain
The BackupAllGPOs.wsf sample backs up all the GPOs in a domain to the specified backup directory. The backup directory must exist. You can use the Comment parameter to specify an optional comment for the backup.
Usage: BackupAllGPOs.wsf <BackupLocation> [/Comment:<Comment>] [/Domain:<DNSDomain>]
Example: BackupAllGPOs.wsf servershareGPOBackups /Comment:'Weekly backup' /Domain:example.microsoft.com
Creating a Copy of a GPO
The CopyGPO.wsf sample creates a new GPO and copies the settings from a source GPO into the new destination GPO. You specify the source GPO either by its name or its GPO ID. You specify the new destination GPO by name. Use the MigrationTable switch to map security principals and paths across domains. Use the CopyACL switch to copy the access control list (ACL) on the source GPO to the destination GPO. To create a migration table, see the Create Migration Table script sample.
Usage: CopyGPO.wsf <SourceGPO> <TargetGPO> [/SourceDomain:<DNSDomainName>] [/TargetDomain:<DNSDomainName>] [/SourceDC:<DomainController>] [/TargetDC<DomainController>] [/MigrationTable<MigrationTable>] [/CopyACL]
Example: CopyGPO.wsf TestPolicyGPO NewProductionGPO /SourceDomain:example.microsoft.com /TargetDomain:example.microsoft.com
Creating a New GPO
The CreateGPO.wsf sample creates a GPO with the specified name in the specified domain.
Usage: CreateGPO.wsf <GPOName> [/Domain:<DNSDomainName>]
Example: CreateGPO.wsf MyGPO /Domain:example.microsoft.com
Creating a Policy Environment Using an XML File
The CreateEnvironmentFromXML.wsf sample reads an XML file that specifies a policy environment, such as an organizational unit (OU) or a GPO.
The script can perform operations such as the following:
- Create GPOs and OUs
- Link GPOs
- Import settings into GPOs
- Set security on GPOs
- Create security groups and users
Using the Undo switch deletes the environment. Specify the ExcludeSettings switch to ignore the GPO templates specified in the XML. Specify the ExcludePermissions switch to ignore the permissions on scopes of management (SOMs) and on GPOs. Default permissions will be used instead. To use a migration table when you import GPOs, specify the MigrationTable switch and the path of the migration table file. Use the MigrationTable switch to map security principals and paths across domains. For more information about how to create a migration table, see the CreateMigrationTable.wsf script sample. Specify the Q switch to enable quiet mode, which suppresses all the confirmation warnings.
Usage: CreateEnvironmentFromXML.wsf /xml:<XmlFile> [/undo] [/Domain:<DNSDomainName>] [/dc:<DomainControllerName>] [/ExcludeSettings] [/ExcludePermissions] [/MigrationTable:<FilePath>]
Example: CreateEnvironmentFromXML.wsf /xml:TestDomain.xml /Domain:/example.microsoft.com /dc:testdomaindc-1 /MigrationTable:TestMigrationTable.xml
Creating an XML File that Represents a Policy Environment
The CreateXMLFromEnvironment.wsf sample reads an existing policy environment; for example, OUs, GPOs, and GPO links. The sample script creates an XML file that represents that environment. You can use this script in conjunction with the CreateEnvironmentFromXML.wsf script. If you do not specify a domain, the domain of the computer is the default.
Multiple switches are available for this script. Use the ExcludePermissions switch so that policy-related permissions are not recorded. Use the StartingOU switch to specify the Lightweight Directory Access Protocol (LDAP) path of an OU from which the XML should be built, rather than parsing the entire domain. Specify the IncludeUsers switch to include user accounts. Use the IncludeAllGroups switch to include groups from the Users container and from the domain root. If you do not specify the IncludeAllGroups switch, the script adds only the groups defined in the OUs to the XML file. If you specify a template path, the GPOs are exported to the specified location. Use the /TemplatePath switch to specify the location in which you want to store the backups of the GPO templates that contain the policy settings.
Usage: CreateXMLFromEnvironment.wsf <OutputFile> [/Domain:<DNSDomainName>] [/dc:<DomainControllerName>] [/TemplatePath:<Path>] [/StartingOU:<LDAPPath>] [/ExcludePermissions] [/IncludeAllGroups] [/IncludeUsers]
Example: CreateXMLFromEnvironment.wsf TestDomain.xml /Domain:example.microsoft.com
Example: CreateXMLFromEnvironment.wsf TestDomain.xml /StartingOU:OU=marketing,DC=MyDomain,DC=COM
Example: CreateXMLFromEnvironment.wsf TestDomain.xml /templatepath:backups
Create Migration Table
The CreateMigrationTable.wsf sample creates a file that contains the XML representation of the paths and the security principals for the specified GPO source.
You can specify one of the following GPO sources:
- An individual GPO
- A backup location
- All the GPOs in a domain
Then, you can use the resulting XML when you perform GPO import and copy operations, which are typically performed across domains.
You can use the following switches:
- Use the GPO switch to use a single GPO source when you build the XML migration table.
- Use the BackupLocation switch to use GPO backups as a source when you build the XML migration table.
- Use the AllGPOs switch to use all the GPOs in the domain as a source to build the XML migration table.
- Use the Overwrite switch to overwrite an existing XML file instead of appending to it.
- Use the MapByName switch to specify a corresponding account with the same name as the original in the destination domain.
Usage: CreateMigrationTable.wsf <TableName> [/GPO:<GPO Name>] [/BackupLocation:<FilePath>] [/AllGPOs] [/Overwrite] [/MapByName] [/Domain:<DNSDomainName>]
Example: CreateMigrationTable.wsf SampleTable.xml /BackupLocation:c:GPOBackups /OverWrite /MapByName
Example: CreateMigrationTable.wsf SampleTable.xml /GPO:TestGPO
Example: CreateMigrationTable.wsf SampleTable.xml /AllGPOs /Overwrite /Domain:example.microsoft.com
Deleting a GPO
The DeleteGPO.wsf sample deletes a GPO. You can specify the GPO by name or by its GPO ID. If you do not specify the KeepLinks parameter, all the links to the GPO in the specified domain and in any sites are deleted.
Usage: DeleteGPO.wsf <GPOName> [/KeepLinks] [/Domain:<DNSDomainName>]
Example: DeleteGPO.wsf MyGPO
Grant Permissions for all GPOs in a Domain
The GrantPermissionOnAllGPOs.wsf sample takes a particular domain and then grants a user or a group the specified level of permission for all the GPOs in that domain. This sample grants the specified level of permission regardless of whether those GPOs are linked to an OU or not. Use the Permission switch to specify a permission level of Read, Apply, Edit, FullEdit, or None for the security principal specified in the GroupName parameter. Use the Replace switch to remove existing permissions for the group or user before you make the change. If a group or a user is already granted a permission level that is higher than the new permission level, and you do not specify the Replace switch, no change is made.
Consider the following example:
- The new permission level is Edit
- The user already has Full Edit permission
In this example, if you do not use the Replace switch, the user retains the Full Edit permission because the change is not applied
Usage: GrantPermissionOnAllGPOs.wsf <Group Name> /Permission: <Permission Level> [/Replace] [/Domain:<DNSDomainName>]
Example: GrantPermissionOnAllGPOs.wsf 'Marketing Group Administrators'/Permission:FullEdit /Replace
Example: GrantPermissionOnAllGPOs.wsf TestUser /Permission:Read
Importing a GPO
The ImportGPO.wsf sample imports the settings from a backup GPO to another GPO that you specify. Use the BackupLocation parameter to specify the location of the backup. Then, use the BackupID parameter to specify the GPO name or backup ID (GUID) of the backup to use. If you do not specify a GPO, the name of the GPO that was backed up will be used.
If you specify a GPO name or a GPO ID for the BackupID parameter, the script imports the most recent backup. To import an earlier version of a GPO backup, specify the unique backup ID for the backup. The unique backup ID is the string that uniquely identifies the backup within its backup directory. To retrieve the unique backup IDs for all the GPOs in a specific backup location, run the QueryBackupLocation.wsf script.
Specify the GPO to which you are importing the setting by using the TargetGPO parameter. Use the optional MigrationTable switch when you import a GPO to map security principals and paths across domains. If the specified GPO does not exist, use the CreateIfNeeded switch to create a new GPO.
Usage: ImportGPO.wsf <BackupLocation> <BackupID> [TargetGPO] [/MigrationTable:<FilePath>] [/CreateIfNeeded] [/Domain:<DNSDomainName>]
Example: ImportGPO.wsf f:backup TestGPO NewGPO /CreateIfNeeded
Example: ImportGPO.wsf f:backup {73624CC9-E8F2-4F05-88D2-193FAE8773CE} NewGPO /CreateIfNeeded
Importing Multiple GPOs into a Domain
The ImportAllGPOs.wsf sample creates new GPOs in a specified domain and imports settings into these new GPOs from a specified backup location. The script creates a new GPO and imports settings for the latest version of each backed-up GPO in the backup location. The names of the GPOs that were backed up are used for the new GPOs. The new GPOs are derived from a previous GPO backup. Therefore, if the previous GPOs still exist in the domain, they will be overwritten by the new GPOs. Any GPO settings that have been changed since the backup will be lost.
Usage: ImportAllGPOs.wsf <BackupLocation> [/MigrationTable:<FilePath>] [Domain:<DNSDomainName>]
Example: ImportAllGPOs.wsf f:backup /MigrationTable:f:Table1.xml
Restoring a GPO
The RestoreGPO.wsf sample restores a backup GPO to the original domain from which it was saved. If the original domain is unavailable, the RestoreGPO.wsf sample fails. Use the BackupLocation parameter to specify the location of the backup. Then, use the BackupID parameter to specify the GPO name or the backup ID (GUID) of the backup to use.
If you specify a GPO name or a GPO ID for the Backup parameter, the script restores the most recent backup. To restore an earlier version of a GPO backup, specify the unique backup ID for the backup. The unique backup ID is the string that uniquely identifies the backup in its backup directory. To retrieve the unique backup IDs for all the GPOs in a backup location, run the QueryBackupLocation.wsf script.
Usage: RestoreGPO.wsf <BackupLocation> <BackupID> [/Domain:<Domain>] [/DC:<DomainController>]
Examples: RestoreGPO.wsf f:backup BackUpGPO
RestoreGPO.wsf f:backup {73624CC9-E8F2-4F05-88D2-193FAE8773CE}
Restoring all GPOs in a Domain
The RestoreAllGPOs.wsf sample restores the most recent backup of each GPO that is backed up to Active Directory in a specified backup location.
Usage: RestoreAllGPOs.wsf <BackupLocation> [/Domain:<DNSDomainName>]
Examples: RestoreAllGPOs.wsf f:backup /Domain:example.microsoft.com
Setting GPO Permissions
The SetGPOPermissions.wsf sample takes a GPO name or GPO ID, group or user name, and permission level and grants that level of permission on the GPO. Use the Permission switch to specify a permission level of Read, Apply, Edit, FullEdit, or None for the security principal that is specified in the GroupName parameter. Use the Replace switch to remove the existing permissions for the group or user before you make the change. Otherwise, the script ensures that the group or user has at least the specified permission level.
Usage: SetGPOPermissions.wsf:<GPOName><GroupName> /Permission:<PermissionLevel> [/Replace] [/Domain:<DNSDomainName>]
Example: SetGPOPermissions.wsf TestGPO TestGroup /Permission:Edit
Example: SetGPOPermissions.wsf TestGPO TestGroup /Permission:Edit
Example: SetGPOPermission.wsf {73624CC9-E8F2-4F05-88D2-193FAE8773CE}TestUser /Permission:FullEdit /Replace /Domain:example.microsoft.com
Setting Permissions for All GPOs Linked to a Scope of Management
The SetGPOPermissionsBySOM.wsf sample grants a user or group a specified permission level for all the GPOs that are linked to a specified SOM (a site, a domain, or an OU). Use the Permission switch to specify a permission level of Read, Apply, Edit, FullEdit, or None for the security principal that is specified in the GroupName parameter. Use the Replace switch to remove existing permissions for the group or user before you make the change. If a group or a user has a permission level that is higher than the new permission level, and you do not specify the Replace switch, no change is made.
Consider the following example:
- The new permission level is Edit
- The user already has Full Edit permission
In this example, if you do not use the Replace switch, the user retains the Full Edit permission because the change is not applied. Use the Recursive switch to apply the change to all the child OUs of the specified SOM.
Usage: SetGPOPermissionsBySOM.wsf <SOM Name> <Group Name> /Permission: <PermissionLevel> [/Recursive] [/Replace] [/Domain:<DNSDomainName>]
Example: SetGPOPermissionsBySOM.wsf 'Marketing Group Administrators' 'Marketing Group' /Permission:FullEdit /Recursive
Example: SetGPOPermissionsBySOM.wsf MarketingOU TestUser /Permission:Read /Replace
Setting Permissions to Create GPOs
The SetGPOCreationPermissions.wsf sample grants or removes the permissions that let a user or security group create GPOs in a domain.
Usage: SetGPOCreationPermissions.wsf <GroupName> [Remove] [/Domain:<DNSDomainName>]
Example: SetGPOCreationPermissions.wsf 'Policy Administrators'
Example: SetGPOCreationPermissions.wsf TestUser /remove
Setting Policy-related Permissions on a SOM
The SetSOMPermissions.wsf sample grants a user or group the specified level of permission on a specified SOM (a site, a domain, or an OU). Use the Permission switch to specify a permission level of LinkGPOs, RSoPLogging, RSoPPlanning, All, or None for the SOM. You can specify either the display name or the full LDAP path of the SOM for the SOM Name parameter. The Inherit switch causes all child containers to inherit the setting. RSoP planning mode requires, at least, a Windows Server domain controller to perform the query, and is not applicable to sites.
Usage: SetSOMPermissions.wsf <SOM Name> <Group Name> /Permission:<PermissionLevel> [/Inherit] [/Domain:<DNSDomainName>]
Example: SetSOMPermissions.wsf 'Test Marketing OU' 'Marketing Admin Group' /Permission:All /Inherit
Example: SetSOMPermission.wsf MarketingOU TestUser /Permission:LinkGPOs
Listing All GPOs in a Domain
The ListAllGPOs.wsf sample prints a list of all the GPOs in the specified domain.
Note
Using the /v switch creates detailed or verbose output for each GPO.
Usage: ListAllGPOs.wsf [/v] [/Domain:<DNSDomainName>]
Example: ListAllGPOs.wsf /v /Domain:example.microsoft.com
Listing Disabled GPOs
The FindDisabledGPOs.wsf sample prints a list of all the GPOs that are disabled or partially disabled in the specified domain. This script enumerates both fully and partially disabled GPOs. The results are grouped accordingly.
Usage: FindDisabledGPOs.wsf [/Domain:<DNSDomainName>]
Example: FindDisabledGPOs.wsf /Domain:example.microsoft.com
Listing GPO Information
The DumpGPOInfo.wsf sample prints information for a specified GPO. You can specify the GPO by its name or its GPO ID.
Usage: DumpGPOInfo.wsf GPOName [/Domain:<DNSDomainName>]
Example: DumpGPOInfo.wsf MyGPO /Domain:example.microsoft.com
Listing GPOs at a Backup Location
The QueryBackupLocation.wsf sample prints a list of the GPOs that have been backed up to a specified file system location. For each backed-up GPO, the Verbose switch displays detailed information, such as the ID, the backup time, and any comments.
Usage: QueryBackupLocation.wsf <path> [/Verbose]
Example: QueryBackupLocation.wsf servershareGPOBackups /Verbose
Listing GPOs by Policy Extension
The FindGPOsByPolicyExtension.wsf sample prints a list of all the GPOs in the specified domain for which a specific policy extension is configured. For example, the script prints all the GPOs in the domain for which the Software Installation or Folder Redirection policy extensions are configured. You can specify either the GUID or the display name of the client-side extension. To determine which client-side extensions are registered locally, use the PrintCSE switch.
Usage: FindGPOsByPolicyExtension.wsf <ExtensionID> [/PrintCSE] [/Domain:<DNSDomainName>]
Example: FindGPOsByPolicyExtension.wsf 'Software Installation'
This example lists all the GPOs that define policy settings for the 'Software Installation' policy extension.
Example: FindGPOsByPolicyExtension.wsf /PrintCSE
This example lists all CSEs that are installed locally.
Group Policy Management Console Scripting Samples Download Free
Listing GPOs by Security Group
The FindGPOsBySecurityGroup.wsf sample prints a list of all the GPOs on which a security principal has the specified permission level. Use the Permission switch to specify the permission level (Read, Apply, Edit, or Full Edit) for the security principal that you want to find. If no permission is specified, the script queries for all the GPOs that have the Apply permission level. Use the Effective switch to display the GPOs with a specific set of permissions, whether the permissions are explicitly set or derived as a result of group membership. Use the None switch to display the GPOs that do not have the specified permission for the specified group or user.
Usage: FindGPOsBySecurityGroup.wsf <GroupName> /Permission:<PermissionLevel> [/Effective] [/Domain:<DNSDomainName>] [/None]
Example: FindGPOsBySecurityGroup.wsf 'Domain Administrators' /Permission:Edit /Effective
Listing GPOs orphaned in SYSVOL
The FindOrphanGPOsInSYSVOL.wsf sample finds and then prints all the GPOs in SYSVOL that do not have a corresponding Active Directory source. These GPOs are usually referred to as orphaned GPOs.
Usually, a GPO becomes orphaned through one of the following ways:
- The GPO was deleted directly through ADSI Edit.
- The GPO was deleted by someone who had permissions to delete the GPO in Active Directory, but not in the SYSVOL directory.
In these cases, the Active Directory portion of the GPO is deleted, but the SYSVOL portion of the GPO remains. Use the Domain switch to specify a domain to search for orphaned GPOs.
Usage: FindOrphanGPOsInSYSVOL.wsf [/Domain:<DNSDomainName>]
Example: FindOrphanGPOsInSYSVOL.wsf /Domain:example.microsoft.com
Listing GPOs with Duplicate Names
The FindDuplicateNamedGPOs.wsf sample prints a list of all the GPOs in the specified domain that have duplicate names.
Usage: FindDuplicateNamedGPOs.wsf [/Domain:<DNSDomainName>]
Example: FindDuplicateNamedGPOs.wsf /domain:example.microsoft.com
Listing GPOs Without Security Filtering
The FindGPOsWithNoSecurityFiltering.wsf sample prints a list of all the GPOs for which apply permissions are not set. These GPOs exist, but they are not applied to any computers or users.
Usage: FindGPOsWithNoSecurityFiltering.wsf [/Domain:<DNSDomainName>]
Example: FindGPOsWithNoSecurityFiltering.wsf /Domain:example.microsoft.com
Listing SOM Information
The DumpSOMInfo.wsf sample prints policy information about a specified SOM (a site, a domain, or an OU). The information that is printed includes information about the GPOs that are linked to the SOM and information about the policy permission on that SOM. Use the ShowInheritedLinks switch to show the inherited GPO links for the SOM.
Usage: DumpSOMInfo.wsf <SOM Name> [/ShowInherited] [/Domain:<DNSDomainName>]
Example: DumpSOMInfo.wsf 'Test OU' /ShowInherited /Domain:example.microsoft.com
Listing SOMs With Links to GPOs in External Domains
The FindSOMsWithExternalGPOLinks.wsf sample prints a list of all the SOMs in the specified domain that link to a GPO in a different domain.
Usage: FindsSOMsWithExternalGPOLinks.wsf [/Domain:<DNSDomainName>]
Example: FindsSOMsWithExternalGPOLinks.wsf /Domain:example.microsoft.com
Listing Unlinked GPOs in a Domain
The FindUnlinkedGPOs.wsf sample prints a list of all the GPOs in the specified domain that have no links. Links outside the domain, including site links, are not included in the list.
Usage: FindUnlinkedGPOs.wsf [/Domain:<DNSDomainName>]
Example: FindUnlinkedGPOs.wsf /Domain:example.microsoft.com
Printing the SOM Policy Tree
The ListSOMPolicyTree.wsf sample prints a list of all the SOMs (all of the sites, domains, and OUs) in the specified domain. For each SOM in the list, a list of the GPOs that are linked to it is printed.
Usage: ListSOMPolicyTree.wsf [/Domain:<DNSDomainName>]
Example: ListSOMPolicyTree.wsf /Domain:example.microsoft.com
Generate Reports for all GPOs
How To Access Group Policy
The GetReportsForAllGPOs.wsf sample generates two files for each GPO in the domain. The first file is an XML file that contains information such as details, links, security filtering, WMI filtering, delegation, computer, and user configurations for the GPO. The second file is an HTML representation of the GPO data. Use the ReportLocation parameter to specify the location in which you want to generate the files. Use the Domain switch to specify the domain that you want to run the report against.
Usage: GetReportsForAllGPOs.wsf <ReportLocation> [/Domain:<DNSDomainName>]
Example: GetReportsForAllGPOs.wsf c:reports
Generate Reports for a GPO
The GetReportsForGPO.wsf sample generates two files for a specified GPO or GPO ID in the domain. The first file is an XML file that contains information such as details, links, security filtering, WMI filtering, delegation, computer and user configurations for the GPO. The second file is an HTML representation of the GPO data. Use the ReportLocation parameter to specify the location in which you want to generate the files. Use the Domain switch to specify the domain that you want to run the report against.
Usage: GetReportsForGPO.wsf <GPOName> <ReportLocation> [/Domain:<DNSDomainName>]
Example: GetReportsForGPO.wsf TestGPO c:reports /Domain:test.microsoft.com
Example: GetReportsForGPO.wsf {73624CC9-E8F2-4F05-88D2-193FAE8773CE} c:reports
Active Directory Documents Page
Responsibilities(Word Doc)
The ability to effectively manage a program requires identification and delineation of tasks. This document enumerates the specific duties required of the various levels of administration for active directory.
Determine a Method to Configure Automatic Updates Clients
The ability to get patches and updates is vital to system security. This page, and the two pages it references, provide details on how to setup a system to receive patches and updates from the CSUN WSUS Server in an Active Directory environment and a non-Active Directory environment.
Descriptions of System Services
This document describes the Windows Server 2003 and Windows XP services in alphabetical order. Services that are installed by default are included as well as additional services that can be added to the computer.
Step-by-Step Guide to Managing the Active Directory
(Word Doc)
This Updated guide is provided to TSAG Members as an introduction to the administration of the Active Directory service and the Active Directory Users and Computers snap-in. This snap-in allows you to add, move, delete, and alter the properties for objects such as groups, computers, servers, printers, and shared folders.
Guide to Managing the Active Directory for Enterprise Administrators(Word Doc)
This updated guide is provided to those individuals as an overview of each of the tasks they may be called upon to perform.
Default Domain Policy
Root-NO Group Policy
Root-O Group Policy
These three group policies sit at the root and affect all users and computers. The first two group policies are not over-writable and contain settings that represent current CSUN computer policy. The third group policy contains settings that represent best practice but can be over-written if the organization feels the need to use different settings.
GPO Settings Worksheet for Windows 2000
GPO Settings Worksheet with Explanations
GPO Settings for Windows XP
GPO Settings for Windows XP SP2
GPO Settings for Windows 2003
GPO Settings Worksheet for Windows Vista
(The above links are Excel Spreadsheets)
These spreadsheets list the full set of Group Policy settings described in Administrative Template (.adm) files shipped with Windows. This includes all policy settings supported on Windows 2000, Windows XP Professional, Windows Server 2003, and Windows Vista (.admx). The last three spreadsheets include separate worksheets for each of the .adm (.admx for Vista) files shipped, as well as a consolidated worksheet for easy searching. Using column filters, the spreadsheet allows simple filtering by operating system, component and machine/user configuration, as well as regular text search of keywords through Excel.
Introduction to Group Policy in Windows Server 2003
Introduction to Group Policy in Windows Server 2000
(The above links are Word Docs)
Administrators use Group Policy to define specific configurations for groups of users and computers by creating Group Policy settings. These settings are contained in a Group Policy object (GPO), which is in turn linked to Active Directory containers, such as sites, domains, or OU's. In this way, Group Policy settings are applied to the users and computers in those Active Directory containers. Administrators can configure the users’ work environment once and rely on the system to enforce the policies as defined. This guide helps introduce the reader to Group Policies.
Implementing Registry-Based Group Policy for Applications(Word Doc)
This white paper focuses on implementing registry-based Group Policy for applications that you are developing. This document begins with some details on what registry-based policy is, and when to use it. From there, the steps to develop registry based policy are described. The appendix to this white paper contains a full language reference to the .adm language used to deploy registry based policies.
Registry Guide for Windows(Executable File)
The Registry Guide for Windows provides an extensive range of registry tweaks, tricks & hacks for optimizing, enhancing and securing the Windows XP, 2000, NT, 98, 95 and Windows Me operating systems.
Troubleshooting Group Policy in Windows 2000
(Word Doc)
This white paper explains how IT administrators can troubleshoot Group Policy. It includes sections on using command-line tools, accessing and using logs, common troubleshooting scenarios, solving software installation issues, checklists for troubleshooting, and best practices. This advanced level paper assumes readers are familiar with the fundamentals of Group Policy.
Active Directory Users, Computers, and Groups
The Active Directory service provides user and computer accounts and distribution and security groups. The operating system integrates user, computer, and group security with the Windows security subsystem as a whole. This paper introduces administrators unfamiliar with Windows to the way users, computers, and groups are organized and how user authentication and authorization are used to provide security.
Windows 2000 Group Policy(Word Doc)
This paper is intended for information technology managers and system administrators who are interested in using Group Policy to manage users’ desktop environments. Group Policy includes options for registry-based policy settings, security settings, software installation, scripts, folder redirection, Remote Installation Services, and Internet Explorer maintenance.
Assigning a Logon Script to a User (aka Loopback Policy)
The current setup of our Active Directory prevents the local Administrator from applying settings or scripts to any User objects. This document provides information on how to get around that restriction.
IT Standards for Management of Active Directory Groups and Group Policy Objects
This paper discusses the standards and naming conventions that are being applied to objects in Active Directory.
IT Standards for User Management
This updated web page discusses the standards and conventions that are being applied to user objects in Active Directory.
Network Access: Let Everyone permissions apply to anonymous users
This paper discusses background information for the Anonymous User and provides information on how to change it's group affiliation.

Introducing the Group Policy Management Console
The Group Policy Management Console (GPMC) is designed to help and simplify Group Policy management by providing a single place for managing core aspects of Group Policy. You can think of the GPMC as a one-stop resource for managing your Group Policy needs. This document introduces you to how to use this tool.
Group Policy Management Software
Windows Security Log Encyclopedia by Catagory
Windows Security Log Encyclopedia by Event ID Number
The Security log gives us important information about what others are doing to our machines and our network. Monitoring the logs is an important task that should be performed every day, especially on critical systems. This section gives us insight as to what is meant by the various event.
Group Policy Management Console X64
Understanding Windows Logging
Logging is a very important factor when attempting to decipher what has taken place on a server or within a network. This web page focuses on the importance of monitoring your windows event logs and will highlight the information that is able to be extracted from typical windows logs that help to secure your critical servers.
Group Policy Management Windows 10
Group Policy Settings
This is a view of a group policy as seen in the GPMC with links to explain every setting.
